One can perform updates in the target in mapping using 2 approaches:
- Using a UPDATE STRATEGY transformation
- Configuring Session and defining properties to "Treat all rows as UPDATE"
But both these approach works only when there is a Primary Key defined in the target table. The session will fail when there will not be any key defined in the target.
Alternatively, if you want to perform TARGET updates, with putting condition on COLUMNs not included as PRIMARY KEY in target table, it will not be feasible with out changing the Keys on target table. i.e. If PRIMARY KEY is defined on COLUMN_A in TABLE_A and you want to Update TABLE_A with conditions on or including COLUMN_B
In such cases the UPDATE_OVERRIDE property of TARGET Object can be useful.
- How to access UPDATE_OVERRIDE property?
- Go to Mapping
- Double Clink on the concerned TARGET or edit the Target
- Click on Properties Tab
- The second Transformation Attribute is the property we are looking for
- Syntax for UPDATE_OVERIDE SQL:
UDATE <TARGET TABLE>
SET <COLUMN NAME to be updated> = :TU.<TARGET COLUMN PORT NAME (As in Designer)>
, [Other columns need to be updated]
WHERE <COLUMN NAME to be treated as KEY > = :TU.<corresponding TARGET COLUMN PORT NAME (As in Designer)>
AND [other conditions]
UPDATE EMPL_POST_HIST
SET POST = :TU.POST
, UPDATE_DATE = :TU.UPDATE_DATE
WHERE EMPL = :TU.EMPL
Following is an example showing Problem statement and step by step Instructions, of two approaches, of suggested solution.
Problem Scenario:
- Target table has not defined Primary key
- Informatica target object has no Keys - Since the Database table has not Keys the Imported Object in Informatica will not have any Key in the Target definition
- Original Mapping : The mapping created using this very Target definition
- Defining update logic: configuring session for UPDATE Logic
- Configure session for Treat All Source Row as "UPDATE"
- Configure in the session target property to UPDATE as UPDATE - optional
- The error you will get while execution - the session will fail
Solution:
Approach 1: Using Update in the Target
- Go to properties tab of Target in Mapping:
- Edit the "Update Override" attribute - generate SQL and add where Clause with the column name on which you want to update:
- Please note that you need to remove the very column, used in WHERE clause from the SET Clause list
- Go to Workflow and refresh changes in the mapping and save them
- Execute the Workflow
- Now it has successfully updated the rows:
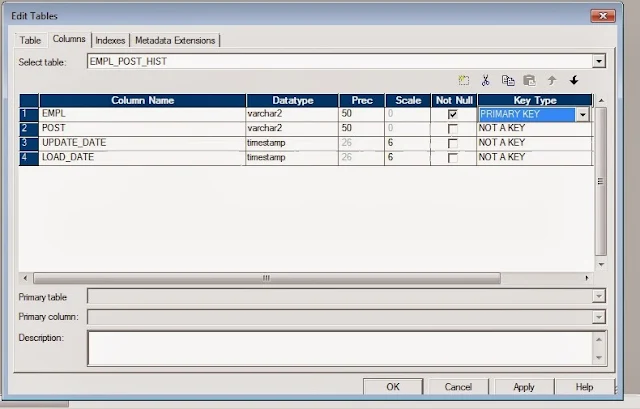
Approach 2: Forcing Keys in the Target object definition in designer
- Edit the Target in the target designer
- Define your Primary key column. Please note that in this case the Database need not have keys defined on the same table:
- Save the changes
- Execute the workflow
- The workflow will update the records in the target table: